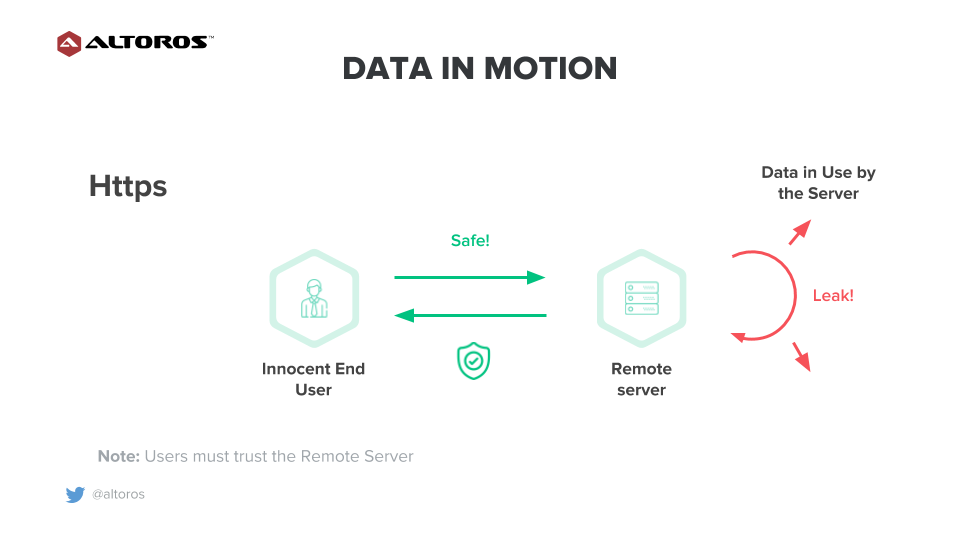
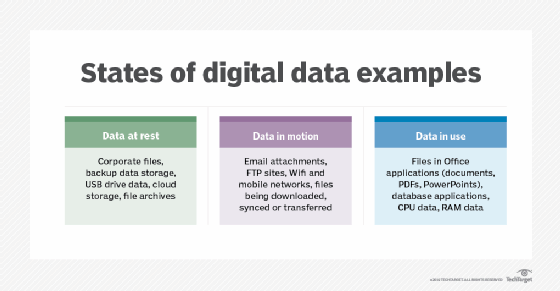
Powering the Next Generation Big Data Architecture for Data-in-Motion and Data-at-Rest - Cisco Blogs
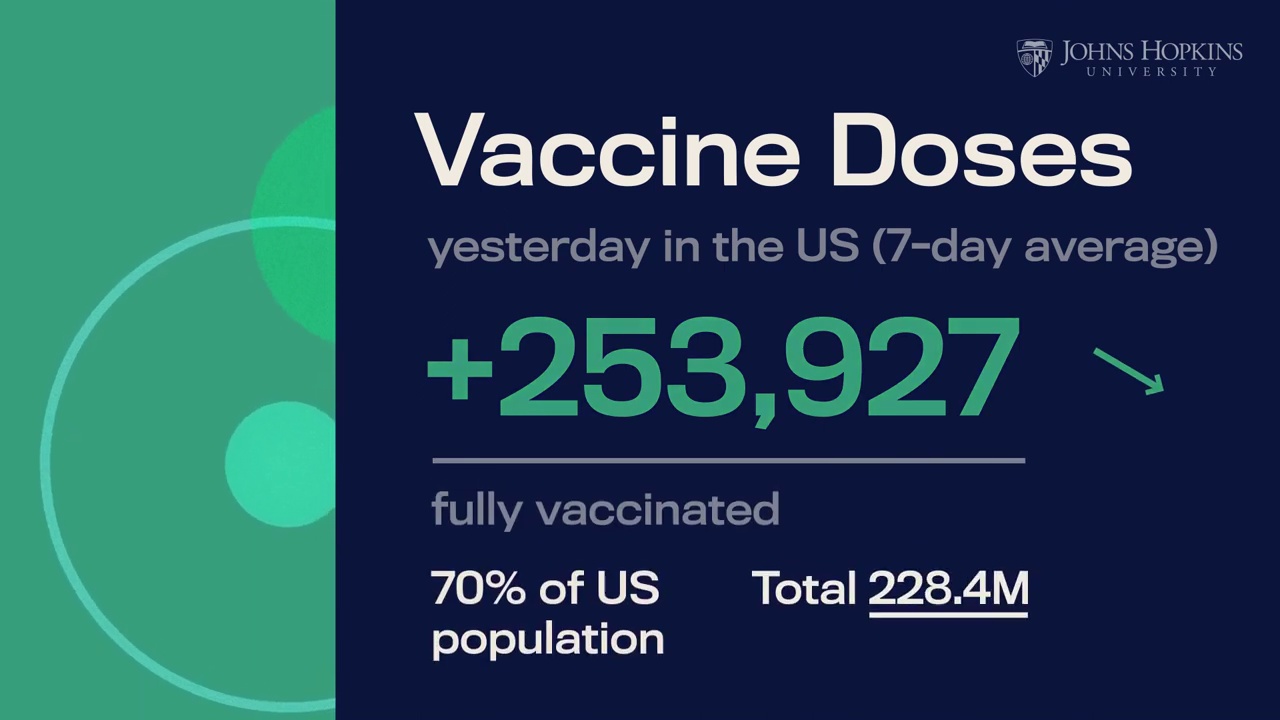
Byte Down: Making Netflix's Data Infrastructure Cost-Effective | by Netflix Technology Blog | Netflix TechBlog
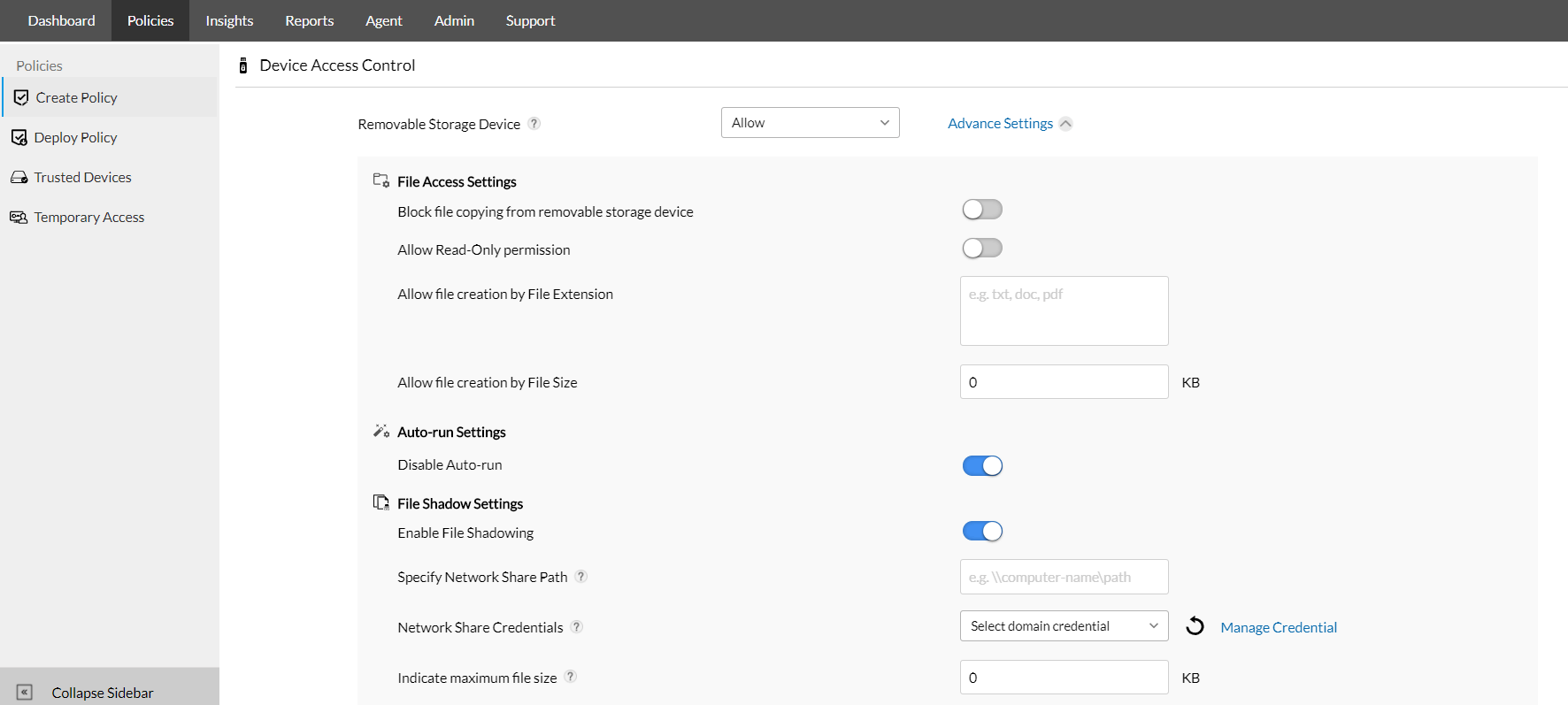
What is Data In Motion? | How to Implement Data In Motion Security - ManageEngine Device Control Plus